𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐞𝐞𝐭𝐬 𝐭𝐡𝐞 𝐌𝐨𝐝𝐞𝐫𝐧 𝐖𝐨𝐫𝐤𝐟𝐨𝐫𝐜𝐞: 𝐀𝐫𝐞 𝐘𝐨𝐮 𝐑𝐞𝐚𝐝𝐲 𝐟𝐨𝐫 𝐋𝐮𝐜𝐲 𝐚𝐧𝐝 𝐇𝐞𝐧𝐫𝐲, 𝐭𝐡𝐞 𝐑𝐨𝐛𝐨𝐭 𝐑𝐞𝐯𝐨𝐥𝐮𝐭𝐢𝐨𝐧.
𝑂𝑢𝑡𝑑𝑎𝑡𝑒𝑑 𝐶𝑦𝑏𝑒𝑟𝑠𝑒𝑐𝑢𝑟𝑖𝑡𝑦 𝑆𝑡𝑟𝑎𝑡𝑒𝑔𝑖𝑒𝑠 𝐴𝑟𝑒 𝐹𝑎𝑖𝑙𝑖𝑛𝑔: 𝐴𝑑𝑎𝑝𝑡𝑖𝑛𝑔 𝑃𝑒𝑜𝑝𝑙𝑒, 𝑃𝑟𝑜𝑐𝑒𝑠𝑠𝑒𝑠, 𝑎𝑛𝑑 𝑇𝑒𝑐ℎ𝑛𝑜𝑙𝑜𝑔𝑦 𝑓𝑜𝑟 𝑎 𝐹𝑢𝑡𝑢𝑟𝑒 𝑤𝑖𝑡ℎ 𝐴𝐼 𝐴𝑔𝑒𝑛𝑡𝑠 𝑎𝑛𝑑 𝑅𝑜𝑏𝑜𝑡𝑠 𝑖𝑛 𝑡ℎ𝑒 𝑊𝑜𝑟𝑘𝑝𝑙𝑎𝑐𝑒.
Mustafa Suleyman, co-founder of DeepMind, offers thought provoking insights in his book The Coming Wave. He explores the transformative impact of AI and large language models (LLMs) on our world, highlighting both the challenges and solutions we must embrace to navigate this rapidly evolving future.
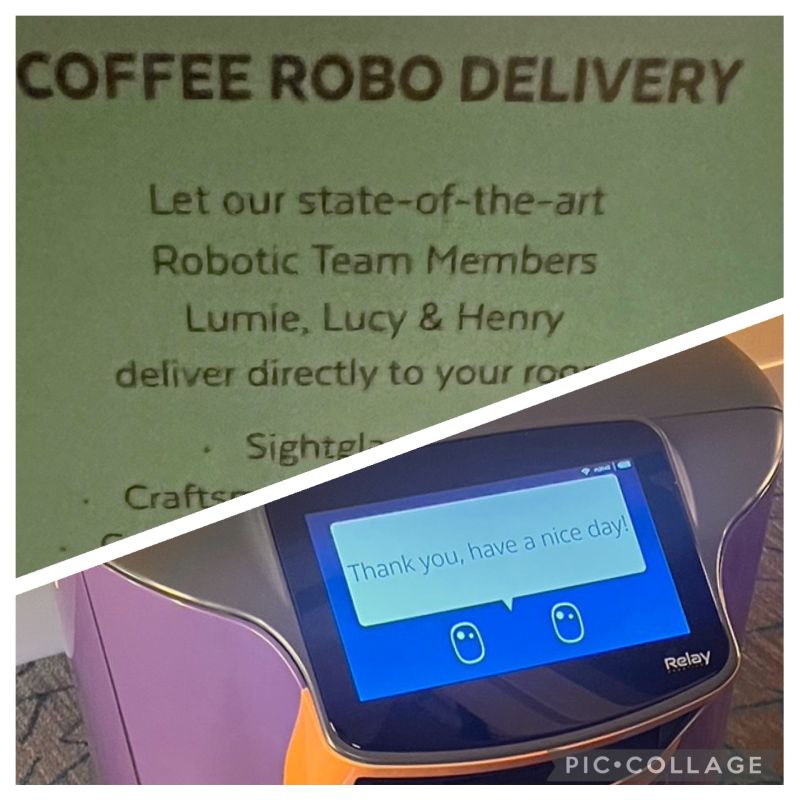
Traveling from Idaho Falls to California, I experienced robot room service during one stay. I tested it by placing three different orders each morning and evening. The deliveries were impressively fast and efficient, sparking my curiosity about service automation and cybersecurity's future.
Rethinking cybersecurity strategies is important in today's evolving workforce due to the transformative presence of AI. As organizations adopt AI, they face unique cybersecurity challenges and must prepare their workforce to adapt effectively. This moment is vital for innovation, strategy, and security.
𝐒𝐭𝐫𝐚𝐭𝐞𝐠𝐢𝐜 𝐀𝐩𝐩𝐫𝐨𝐚𝐜𝐡𝐞𝐬 𝐟𝐨𝐫 𝐁𝐮𝐬𝐢𝐧𝐞𝐬𝐬 𝐋𝐞𝐚𝐝𝐞𝐫𝐬 𝐚𝐧𝐝 𝐂𝐈𝐒𝐎𝐬 𝐭𝐨 𝐀𝐝𝐝𝐫𝐞𝐬𝐬 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐂𝐡𝐚𝐥𝐥𝐞𝐧𝐠𝐞𝐬 𝐢𝐧 𝐭𝐡𝐞 𝐀𝐈 𝐄𝐫𝐚:
➡️ 𝐙𝐞𝐫𝐨 𝐓𝐫𝐮𝐬𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐅𝐫𝐚𝐦𝐞𝐰𝐨𝐫𝐤: Transition to a zero trust model that verifies every user, device, and system interaction within the network.
➡️ 𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐞 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐧𝐭𝐨 𝐀𝐈 𝐃𝐞𝐯𝐞𝐥𝐨𝐩𝐦𝐞𝐧𝐭: Build security into AI models from the ground up to ensure they are resistant to adversarial attacks.
➡️ 𝐂𝐨𝐥𝐥𝐚𝐛𝐨𝐫𝐚𝐭𝐢𝐨𝐧 𝐁𝐞𝐭𝐰𝐞𝐞𝐧 𝐇𝐮𝐦𝐚𝐧𝐬 𝐚𝐧𝐝 𝐀𝐈 𝐀𝐠𝐞𝐧𝐭𝐬: Create policies and workflows that ensure smooth collaboration between human employees, AI agents, and robots.
➡️ 𝐀𝐝𝐨𝐩𝐭 𝐀𝐈 𝐃𝐫𝐢𝐯𝐞𝐧 𝐓𝐡𝐫𝐞𝐚𝐭 𝐃𝐞𝐭𝐞𝐜𝐭𝐢𝐨𝐧: Leverage AI and machine learning to monitor and detect anomalies in real time, allowing for proactive identification of cyber threats.
➡️ 𝐂𝐨𝐥𝐥𝐚𝐛𝐨𝐫𝐚𝐭𝐢𝐨𝐧 𝐰𝐢𝐭𝐡 𝐈𝐧𝐝𝐮𝐬𝐭𝐫𝐲 𝐚𝐧𝐝 𝐆𝐨𝐯𝐞𝐫𝐧𝐦𝐞𝐧𝐭: Partner with industry peers and regulatory bodies to share insights and develop standards for securing AI and robotics.
➡️ 𝐃𝐞𝐯𝐞𝐥𝐨𝐩 𝐈𝐧𝐜𝐢𝐝𝐞𝐧𝐭 𝐑𝐞𝐬𝐩𝐨𝐧𝐬𝐞 𝐏𝐥𝐚𝐧𝐬 𝐟𝐨𝐫 𝐀𝐈 𝐓𝐡𝐫𝐞𝐚𝐭𝐬: Prepare for AI specific threats by creating tailored incident response and recovery plans.
Securing the future of business means rethinking cybersecurity for an AI driven workforce today for business sustainability.