𝐄𝐯𝐨𝐥𝐮𝐭𝐢𝐨𝐧 𝐟𝐫𝐨𝐦 𝐣𝐮𝐬𝐭 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐀𝐜𝐜𝐞𝐬𝐬 𝐂𝐨𝐧𝐭𝐫𝐨𝐥 (𝐍𝐀𝐂) 𝐭𝐨 𝐙𝐞𝐫𝐨 𝐓𝐫𝐮𝐬𝐭 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐀𝐜𝐜𝐞𝐬𝐬 (𝐙𝐓𝐍𝐀) 𝐝𝐫𝐢𝐯𝐞𝐧 𝐛𝐲 𝐢𝐧𝐧𝐨𝐯𝐚𝐭𝐢𝐨𝐧𝐬 𝐥𝐢𝐤𝐞 𝐏𝐞𝐫𝐟𝐢𝐠𝐨'𝐬 𝐂𝐥𝐞𝐚𝐧 𝐌𝐚𝐜𝐡𝐢𝐧𝐞𝐬. 𝐌𝐨𝐝𝐞𝐫𝐧 𝐄𝐧𝐭𝐞𝐫𝐩𝐫𝐢𝐬𝐞𝐬 𝐫𝐞𝐪𝐮𝐢𝐫𝐞 𝐛𝐨𝐭𝐡 𝐜𝐨𝐦𝐩𝐨𝐧𝐞𝐧𝐭𝐬 𝐟𝐨𝐫 𝐚 𝐜𝐨𝐦𝐩𝐫𝐞𝐡𝐞𝐧𝐬𝐢𝐯𝐞 𝐙𝐞𝐫𝐨 𝐓𝐫𝐮𝐬𝐭 𝐀𝐫𝐜𝐡𝐢𝐭𝐞𝐜𝐭𝐮𝐫𝐚𝐥 𝐉𝐨𝐮𝐫𝐧𝐞𝐲.
Assessing Security and Network Access Control from a Threat Actor's Perspective For threat actors, a successful security breach involves more than just gaining initial access. They must maneuver through the network, pinpoint valuable assets, and make the breach profitable. Understanding the significance of controlling or extending to other compromised assets, threat actors allocate tasks or focus on specific areas to breach the infrastructure effectively. This highlights why obtaining VPN access to an organization's infrastructure with compromised credentials has become a common strategy and specialization.
Looking back on earlier NAC and its comparison to modern micro-segmentation methods, we Reflect on past Network Access Control (NAC) practices and compare them to modern micro-segmentation techniques to prevent lateral movement in the case of compromise, a clear evolution in network security and access control methods is evident over the past two decades. Although micro-segmentation appears simple in theory, the intricacies of actual network structures, alongside cloud services and mobile technologies, have highlighted the limitations of traditional approaches. This underscores the importance of implementing thorough end-to-end micro-segmentation for enhanced security architecture and improved infrastructure resilience against design vulnerabilities.
𝐅𝐞𝐰 E𝐚𝐫𝐥𝐲 𝐃𝐚𝐲𝐬 𝐨𝐟 𝐍𝐀𝐂 (𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐀𝐜𝐜𝐞𝐬𝐬 𝐂𝐨𝐧𝐭𝐫𝐨𝐥)
➡️ 𝐏𝐫𝐞-𝐀𝐝𝐦𝐢𝐬𝐬𝐢𝐨𝐧 𝐂𝐨𝐧𝐭𝐫𝐨𝐥: Devices had to meet particular security criteria before gaining network access.
➡️ 𝐏𝐨𝐬𝐭-𝐀𝐝𝐦𝐢𝐬𝐬𝐢𝐨𝐧 𝐂𝐨𝐧𝐭𝐫𝐨𝐥:: Supervising and regulating devices once connected to the network to ensure ongoing compliance with policies.
➡️ 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲-𝐁𝐚𝐬𝐞𝐝 𝐀𝐜𝐜𝐞𝐬𝐬: Access authorization was determined by user identities and roles.
𝐅𝐞𝐰 𝐌𝐢𝐜𝐫𝐨-𝐒𝐞𝐠𝐦𝐞𝐧𝐭𝐚𝐭𝐢𝐨𝐧 𝐓𝐨𝐝𝐚𝐲: 𝐀 𝐙𝐞𝐫𝐨 𝐓𝐫𝐮𝐬𝐭 𝐀𝐩𝐩𝐫𝐨𝐚𝐜𝐡
➡️ 𝐆𝐫𝐚𝐧𝐮𝐥𝐚𝐫 𝐂𝐨𝐧𝐭𝐫𝐨𝐥: Micro-segmentation establishes isolated zones at the application or workload level, limiting communication paths within the network.
➡️ 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐧𝐝 𝐂𝐨𝐧𝐭𝐞𝐱𝐭-𝐀𝐰𝐚𝐫𝐞:: Decisions rely on user identity, device, application, and behavior, not just network location.
➡️ 𝐃𝐲𝐧𝐚𝐦𝐢𝐜 𝐏𝐨𝐥𝐢𝐜𝐲 𝐄𝐧𝐟𝐨𝐫𝐜𝐞𝐦𝐞𝐧𝐭:: Security policies are consistently applied and adjusted in real-time according to context, rather than static regulations.
𝐊𝐞𝐲 𝐂𝐨𝐧𝐭𝐫𝐚𝐬𝐭𝐬: 𝐅𝐥𝐞𝐱𝐢𝐛𝐢𝐥𝐢𝐭𝐲 𝐢𝐧 𝐏𝐨𝐥𝐢𝐜𝐢𝐞𝐬 & 𝐒𝐜𝐨𝐩𝐞 𝐚𝐧𝐝 𝐃𝐞𝐭𝐚𝐢l.
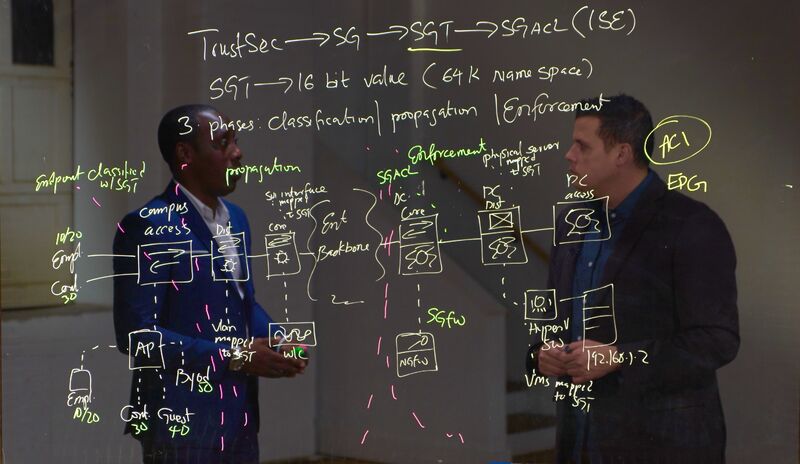
- By Admin
- May 31, 2025